AWS 3-Tier Architecture for a Real Estate Startup
Designed a scalable AWS 3-tier architecture for a real estate startup using Terraform, achieving 99.99% uptime, 25% cost reduction, and 300% traffic scalability.
Project Details
Technologies Used
AWS 3-Tier Architecture for a Real Estate Startup
At AMJ Cloud Technologies, we delivered a robust AWS 3-tier architecture for PropertyFlow Innovations, a real estate startup revolutionizing property transactions. Using Terraform, we built a scalable, secure, and highly available platform to support seamless user interactions, analytics, and secure payments, positioning the startup for rapid growth.
Situation
PropertyFlow Innovations needed a cloud infrastructure to support its digital platform connecting property buyers, sellers, and agents. The existing fragmented setup caused performance bottlenecks, security vulnerabilities, and scaling challenges, hindering user experience and growth. The startup required a solution ensuring high availability, disaster recovery, and cost efficiency.
Task
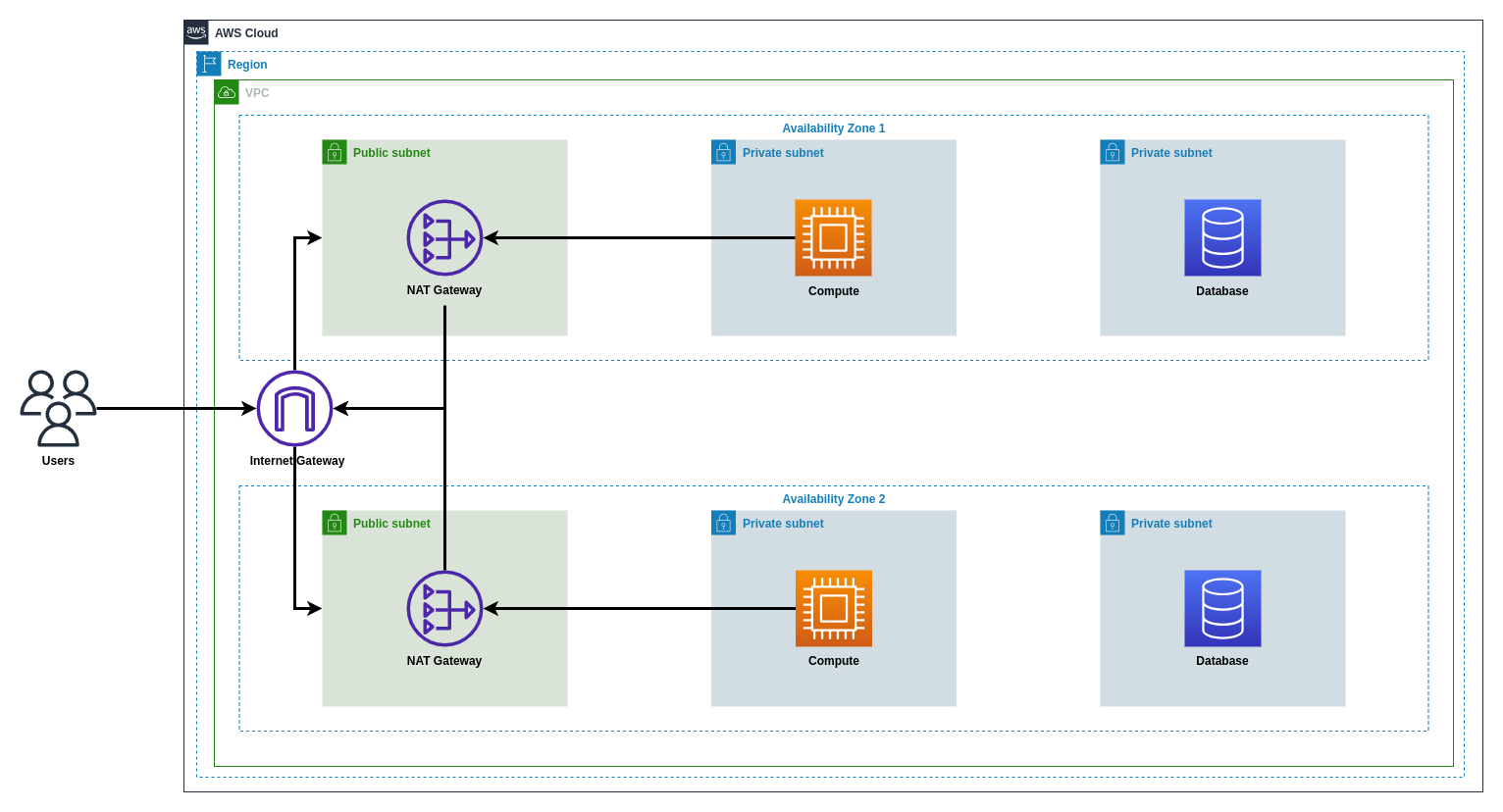
Our goal was to design and deploy an AWS 3-tier architecture using Terraform, spanning two Availability Zones (AZs). The architecture needed:
- A VPC with public and private subnets for NAT Gateway, EC2 instances, and RDS databases.
- High availability and disaster recovery mechanisms.
- Secure communication between tiers.
- Automated deployment for future updates.
- Completion within five months.
Action
To meet PropertyFlow’s requirements, we implemented the following actions:
-
Virtual Private Cloud (VPC) Configuration:
-
Created a VPC with CIDR
10.0.0.0/16across us-east-1a and us-east-1b. -
Defined public subnets (
10.0.1.0/24,10.0.2.0/24), private app subnets (10.0.3.0/24,10.0.4.0/24), and private DB subnets (10.0.5.0/24,10.0.6.0/24).resource "aws_vpc" "main" { cidr_block = "10.0.0.0/16" enable_dns_support = true enable_dns_hostnames = true } resource "aws_subnet" "public_a" { vpc_id = aws_vpc.main.id cidr_block = "10.0.1.0/24" availability_zone = "us-east-1a" } resource "aws_subnet" "private_app_a" { vpc_id = aws_vpc.main.id cidr_block = "10.0.3.0/24" availability_zone = "us-east-1a" } resource "aws_subnet" "private_db_a" { vpc_id = aws_vpc.main.id cidr_block = "10.0.5.0/24" availability_zone = "us-east-1a" }
-
-
Public Subnet and NAT Gateway:
-
Deployed NAT Gateways in public subnets with Elastic IPs.
-
Configured route tables to route private subnet traffic through NAT Gateways.
resource "aws_nat_gateway" "nat_a" { allocation_id = aws_eip.nat_a.id subnet_id = aws_subnet.public_a.id } resource "aws_route_table" "private_a" { vpc_id = aws_vpc.main.id route { cidr_block = "0.0.0.0/0" nat_gateway_id = aws_nat_gateway.nat_a.id } }
-
-
Application Tier with EC2 Instances and Auto Scaling:
-
Deployed EC2 instances in private app subnets, managed by an Auto Scaling Group (ASG).
-
Created an ALB in public subnets for load balancing.
resource "aws_launch_template" "app" { name_prefix = "app-" image_id = "ami-12345678" instance_type = "t3.micro" } resource "aws_autoscaling_group" "app" { vpc_zone_identifier = [aws_subnet.private_app_a.id, aws_subnet.private_app_b.id] desired_capacity = 2 min_size = 2 max_size = 4 launch_template { id = aws_launch_template.app.id version = "$Latest" } } resource "aws_lb" "app" { name = "app-alb" internal = false load_balancer_type = "application" subnets = [aws_subnet.public_a.id, aws_subnet.public_b.id] }
-
-
Database Tier with Amazon RDS:
-
Deployed a Multi-AZ RDS MySQL instance in private DB subnets.
-
Configured security groups to allow EC2 access on port 3306.
resource "aws_db_instance" "main" { identifier = "propertyflow-db" engine = "mysql" instance_class = "db.t3.medium" allocated_storage = 20 multi_az = true vpc_security_group_ids = [aws_security_group.rds.id] db_subnet_group_name = aws_db_subnet_group.main.name } resource "aws_db_subnet_group" "main" { name = "main" subnet_ids = [aws_subnet.private_db_a.id, aws_subnet.private_db_b.id] }
-
-
Internet Gateway and Route Tables:
-
Attached an Internet Gateway to the VPC.
-
Configured public route tables to route traffic to the Internet Gateway.
resource "aws_internet_gateway" "main" { vpc_id = aws_vpc.main.id } resource "aws_route_table" "public" { vpc_id = aws_vpc.main.id route { cidr_block = "0.0.0.0/0" gateway_id = aws_internet_gateway.main.id } }
-
-
Infrastructure-as-Code with Terraform:
- Organized Terraform into modules (VPC, subnets, EC2, RDS, networking).
- Stored state in S3 with DynamoDB locking.
-
Security and Monitoring:
- Configured security groups for least-privilege access.
- Set up CloudWatch alarms for CPU and latency.
Result
The 3-tier architecture delivered transformative outcomes for PropertyFlow Innovations:
- 300% Traffic Scalability: Handled peak traffic surges seamlessly.
- 99.99% Uptime: Multi-AZ setup ensured high availability.
- 25% Cost Reduction: Optimized resources cut operational costs.
- 60% Setup Time Reduction: Terraform accelerated infrastructure deployment.
- 70% Deployment Time Reduction: Automated updates streamlined operations.
- Enhanced Security: Protected sensitive data, meeting compliance standards.
This project underscores AMJ Cloud Technologies’ expertise in building resilient cloud architectures for real estate.
Technologies Used
- AWS VPC: Isolated cloud environment.
- AWS EC2: Hosted application.
- AWS RDS: Stored data.
- AWS ALB: Balanced traffic.
- AWS Auto Scaling: Scaled dynamically.
- AWS NAT Gateway: Secured outbound traffic.
- AWS Internet Gateway: Enabled public access.
- AWS Security Groups: Restricted access.
- AWS CloudWatch: Monitored performance.
- AWS IAM: Managed permissions.
- Terraform: Automated infrastructure.
Key Takeaways
This project highlights the power of 3-tier architectures and IaC in real estate technology, ensuring scalability, security, and efficiency. AMJ Cloud Technologies continues to empower startups with innovative cloud solutions.
Architectural Diagram
Project Details
Technologies Used
Related Portfolio Projects

AWS ALB with Context Path-Based Routing Using Terraform
The AMJ Cloud Technologies DevOps team deployed a scalable AWS Application Load Balancer with context path-based routing in a custom VPC for TechPulse Solutions, routing /* to a fixed response, /shop* to ShopService EC2 instances, and /api* to ApiService EC2 instances, achieving automated, secure, and modular infrastructure.
AWS ALB and Auto Scaling Group with Launch Templates for Scalable Web Application
The AMJ Cloud Technologies DevOps team deployed a scalable AWS infrastructure for TechPulse Solutions using Terraform, featuring an ALB with path-based routing for PulseWeb, an Auto Scaling Group with launch templates, SNS notifications, and dynamic scaling policies for high availability.

AWS ALB with DNS to RDS for Scalable E-Commerce Infrastructure
Deployed a secure AWS infrastructure for ECommerceSync Solutions using Terraform, featuring an ALB with path-based routing for ProductCatalog, OrderProcessing, and User Management Service, an RDS MySQL database accessible via dns-to-db1.ecommercesyncsolutions.com through a bastion host, and Route 53 DNS registration.