Designing Scalable and Secure Network Architectures with AWS VPC
Developed a scalable and secure AWS VPC architecture using Terraform, reducing provisioning time by 60% and ensuring robust network isolation and compliance.
Project Details
Technologies Used
Designing Scalable and Secure Network Architectures with AWS VPC
At AMJ Cloud Technologies, we conducted an internal R&D initiative to design robust and secure Virtual Private Cloud (VPC) environments in AWS. This case study showcases our expertise in simplifying complex AWS networking components, creating a repeatable blueprint for secure, scalable, and compliant network architectures suitable for clients from startups to enterprises.
Situation
AWS Virtual Private Cloud (VPC) enables organizations to build isolated network environments in the cloud, but designing a VPC that balances security, scalability, and manageability is complex. Challenges include ensuring proper resource isolation, enabling secure internet access, implementing layered security, and supporting hybrid cloud scenarios. AMJ Cloud Technologies aimed to develop a modular VPC architecture that addresses these challenges, providing a standardized framework to streamline client deployments while meeting compliance and performance requirements.
Task
Our team was tasked with creating a scalable and secure AWS VPC architecture to serve as a reusable blueprint. The objectives were:
- Support separation of public and private resources for enhanced security.
- Enable controlled internet access for public and private subnets.
- Implement layered security using Security Groups and Network ACLs.
- Ensure scalability across Availability Zones (AZs) and regions.
- Support hybrid cloud use cases for integration with on-premises infrastructure.
- Reduce provisioning time and ensure consistency using Infrastructure as Code.
The project was executed by a team of cloud engineers and network specialists over a two-month timeline.
Action
To achieve these objectives, we systematically designed and tested a modular AWS VPC architecture, leveraging AWS best practices and Terraform for automation:
-
CIDR Block Assignment:
- Assigned a CIDR block of
10.0.0.0/16, providing 65,535 IP addresses for subnetting to prevent IP exhaustion. - Planned non-overlapping subnet ranges to avoid routing conflicts.
- Assigned a CIDR block of
-
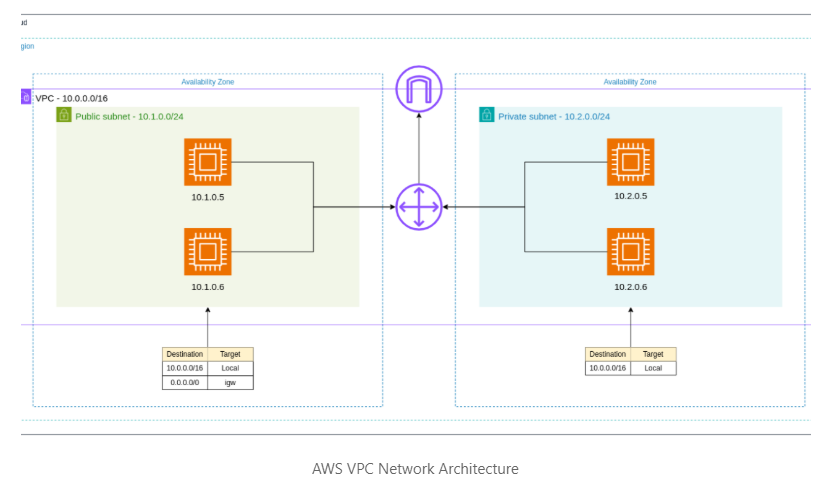
Subnet Design:
- Segmented the VPC into public and private subnets across multiple Availability Zones:
- Public Subnets: Hosted web servers, NAT gateways, and bastion hosts (e.g.,
10.0.1.0/24,10.0.2.0/24). - Private Subnets: Hosted application servers, databases, and internal services (e.g.,
10.0.3.0/24,10.0.4.0/24).
- Public Subnets: Hosted web servers, NAT gateways, and bastion hosts (e.g.,
- Distributed subnets across three AZs for high availability.
- Segmented the VPC into public and private subnets across multiple Availability Zones:
-
Internet Connectivity:
- Attached an Internet Gateway (IGW) to the VPC, linked to public subnet route tables for direct internet access.
- Deployed NAT Gateways in public subnets to enable outbound internet access from private subnets while blocking inbound traffic.
-
Routing Policies:
- Configured public subnet route tables to direct
0.0.0.0/0traffic to the IGW. - Configured private subnet route tables to route internet-bound traffic through the NAT Gateway.
- Evaluated AWS Transit Gateway for inter-VPC and multi-region communication.
- Configured public subnet route tables to direct
-
Security Enforcement:
- Implemented Security Groups (SGs) for least-privilege access control at the instance level.
- Applied Network ACLs (NACLs) at the subnet level for stateless traffic filtering to enhance security.
- Validated rules to ensure compliance with organizational security standards.
-
IPv6 Consideration:
- Configured Egress-Only Internet Gateways for private IPv6 resources, ensuring outbound-only connectivity.
- Tested IPv6 compatibility for future-proofing.
-
DHCP Option Sets:
- Used custom DHCP Option Sets to define internal DNS resolution and naming conventions aligned with organizational standards.
-
Monitoring with VPC Flow Logs:
- Enabled VPC Flow Logs for all subnets to audit traffic, detect anomalies, and assist with troubleshooting.
- Integrated logs with monitoring tools for real-time analysis.
-
Secure Remote Access:
- Deployed bastion hosts in public subnets with strict SSH access control via key pairs for secure access to private subnet resources.
- Implemented auditing for remote access.
-
Infrastructure as Code:
- Developed a Terraform template to automate VPC provisioning, ensuring consistency and reducing setup time.
- Versioned Terraform scripts in a Git repository for collaboration and traceability.
The team conducted iterative testing, simulated multi-AZ failover scenarios, and reviewed configurations to align with AWS best practices.
Result
The AWS VPC design initiative delivered significant outcomes:
- 60% Provisioning Time Reduction: Terraform templates streamlined environment setup, cutting provisioning time by 60%.
- Consistent Security Policies: Security Groups and NACLs ensured compliance across public and private tiers.
- Multi-AZ and Multi-Region Scalability: Subnet distribution and Transit Gateway evaluation supported high availability and regional expansion.
- Enhanced Isolation: Public and private subnet separation reduced attack surfaces.
- Hybrid Cloud Readiness: The architecture supported integration with on-premises data centers via Transit Gateway and VPN.
This reusable VPC blueprint has been adopted internally as a foundation for client projects, enabling AMJ Cloud Technologies to deliver secure and scalable AWS networking solutions. The initiative strengthened our team’s expertise in cloud infrastructure design.
Technologies Used
- AWS VPC: Provided isolated network environments.
- Terraform: Automated infrastructure provisioning.
- Security Groups: Enforced instance-level access control.
- Network ACLs: Enabled subnet-level traffic filtering.
- NAT Gateway: Facilitated secure outbound internet access.
- Internet Gateway: Enabled direct internet access for public subnets.
- Transit Gateway: Supported inter-VPC and multi-region connectivity.
- VPC Flow Logs: Monitored and audited network traffic.
Key Use Cases
This VPC architecture is suitable for:
- Multi-tier application deployments requiring isolated workloads.
- Hybrid connectivity with on-premises data centers.
- Regulated environments needing granular network control.
Key Takeaways
This case study underscores the importance of modular VPC design in achieving secure, scalable, and manageable AWS network architectures. Strategic subnetting, layered security, and Infrastructure as Code streamline deployments and ensure compliance. AMJ Cloud Technologies is committed to empowering organizations with resilient cloud networking solutions.
Architectural Diagram
Project Details
Technologies Used
Related Case Studies

Deploying a Scalable E-commerce Platform with Kubernetes
Deployed a scalable e-commerce platform using Kubernetes on EKS, achieving zero-downtime updates, automated scaling, and secure microservice communication.
Read Case Study
Accelerating Global Content Delivery with Amazon CloudFront
Enhanced global content delivery for a SaaS client using Amazon CloudFront, improving load times by 60% and reducing infrastructure load by 40%.
Read Case Study
AWS Load Balancer Controller - Ingress Groups for VividCart Solutions
AMJ Cloud Technologies deployed Ingress Groups with the AWS Load Balancer Controller on EKS for VividCart Solutions, merging multiple Ingress resources into a single ALB for secure e-commerce microservices.
Read Case Study